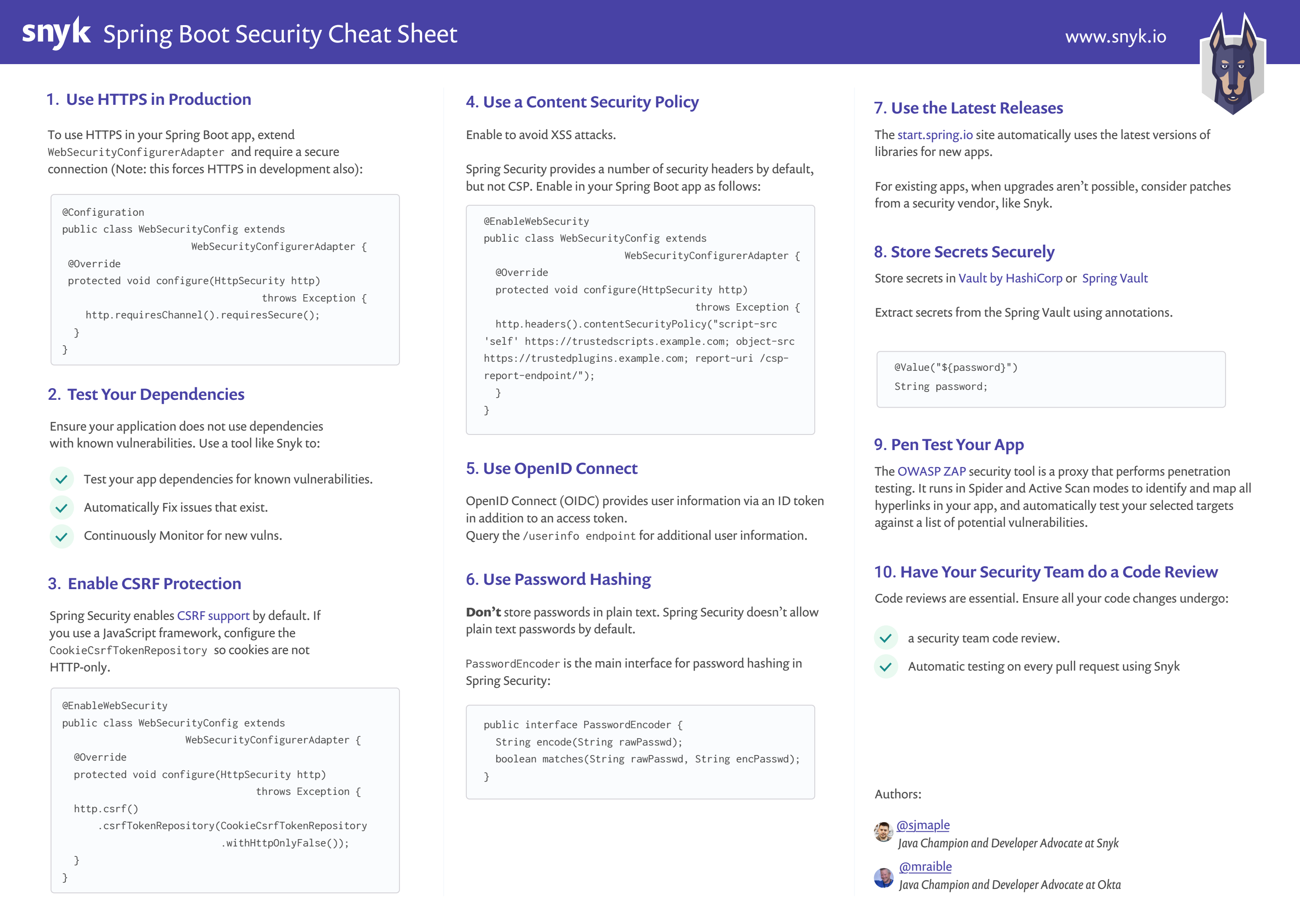
![OWASP Top 10 Application Security Risks Cheat Sheet by [deleted] - Download free from Cheatography - Cheatography.com: Cheat Sheets For Every Occasion OWASP Top 10 Application Security Risks Cheat Sheet by [deleted] - Download free from Cheatography - Cheatography.com: Cheat Sheets For Every Occasion](https://media.cheatography.com/storage/thumb/deleted-2754_owasp-top-10-application-security-risks.750.jpg)
OWASP Top 10 Application Security Risks Cheat Sheet by [deleted] - Download free from Cheatography - Cheatography.com: Cheat Sheets For Every Occasion

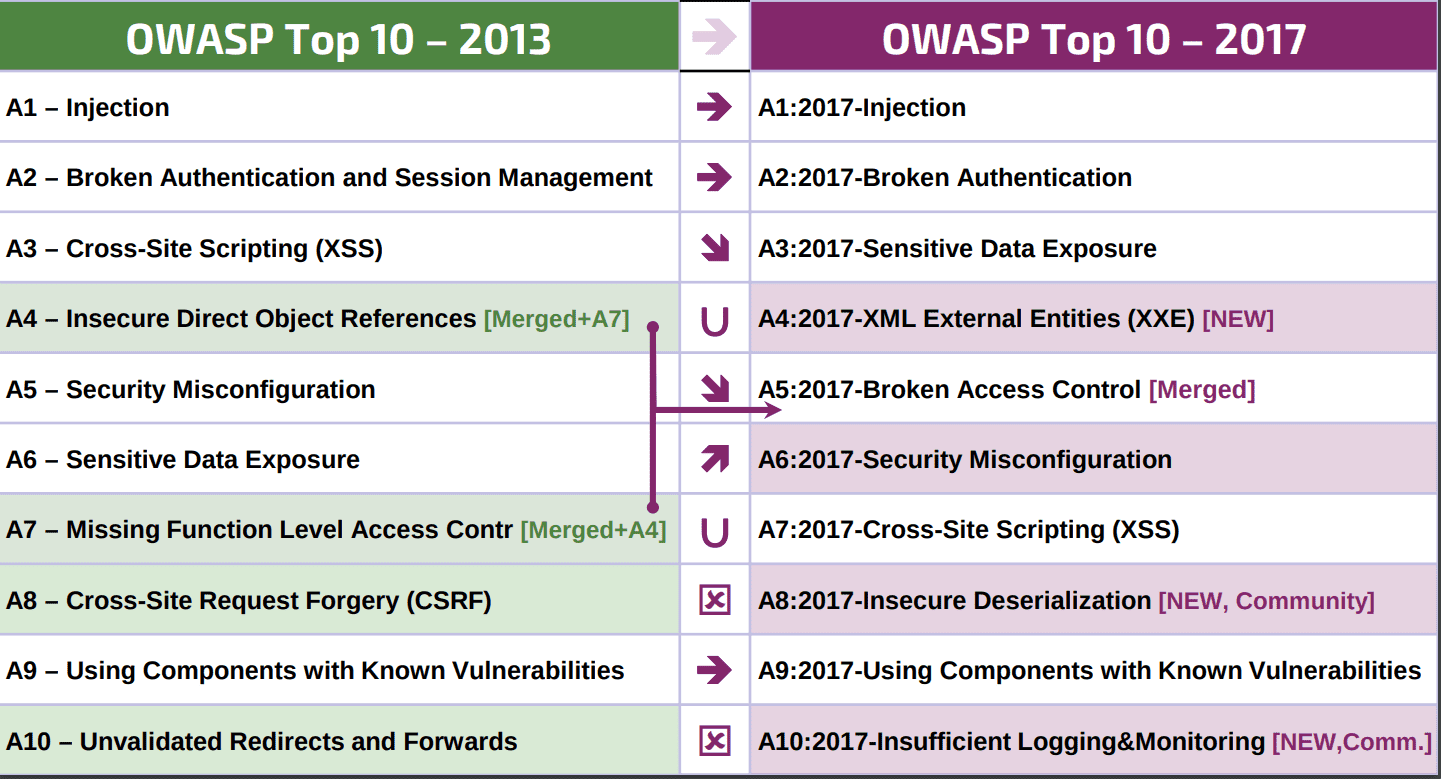
OWASP Top 10 Application Security Risks - 2017 | Security, 10 things, Coding | Software security, Security, 10 things

Security Compass on Twitter: "Check out our OWASP Top Ten Cheat Sheet, a quick way to learn the most common web application vulnerabilities as well as the defenses used to manage them:
![Tinker on Twitter: "Cheatsheet for OWASP Top Ten. [ Source: Page 6 of the official PDF - https://t.co/G4iGuy7hJH (pdf) ]… https://t.co/FOlWVpkX7i" Tinker on Twitter: "Cheatsheet for OWASP Top Ten. [ Source: Page 6 of the official PDF - https://t.co/G4iGuy7hJH (pdf) ]… https://t.co/FOlWVpkX7i"](https://pbs.twimg.com/media/ECpxIn1XYAU1BZO.jpg:large)